Both Internet users and Internet-connected applications can benefit from investing in cybersecurity. One core aspect of online privacy is the use of a proxy server, though this basic building block may not be initially visible underneath its more recognizable forms. Proxy servers are a useful thing …

This, in fact, was my first post written entirely in Vim! I typically use Visual Studio Code but recently decided to become more comfortable with keyboard shortcuts. In the process I got more accustomed to visual mode, and finally got around to figuring out buffers. 😅
Remarkably, now when I go back …

Last week, I wrote about the importance of properly handling user input in our websites and applications. I alluded to an overarching security lesson that I hope to make explicit today: the security of our software, application, and customer data is built from the ground up, long before the product …

Software developers have a lot on their minds. There are are myriad of questions to ask when it comes to creating a website or application: What technologies will we use? How will the architecture be set up? What functions do we need? What will the UI look like? Especially in a software market where …

While not the brightest of the bunch, Bob’s rendition of “I will always love you” at karaoke night had everyone blown away.


Well, my afternoon is booked.


I prefer, “move at a reasonably maintainable fast speed while breaking things and then fixing them” but I guess that’s too long to be a sticker.

TIL: https://tools.ietf.org/html/rfc1178
My next computer will be named “whos-on-first”.

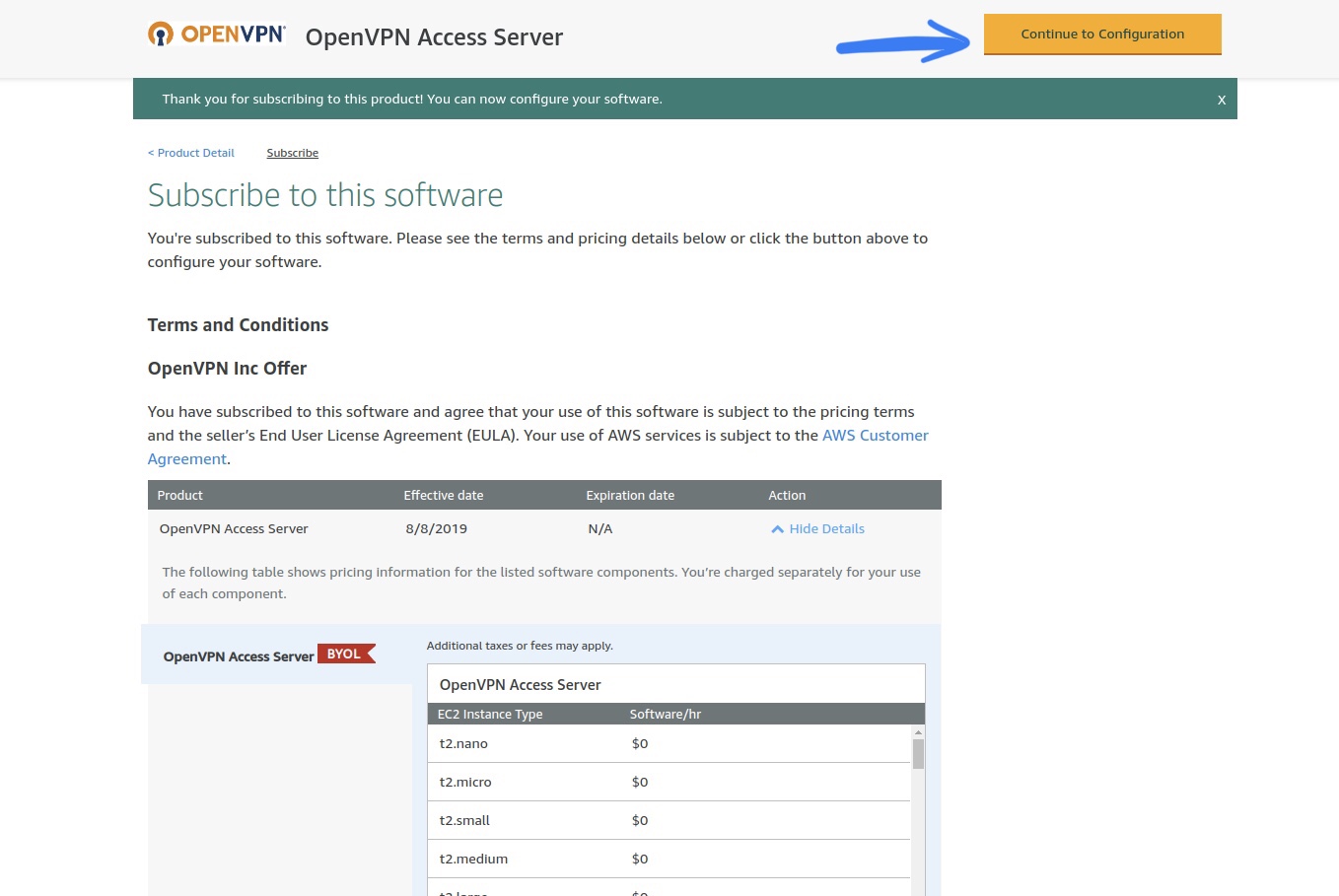
Rolling your own Virtual Private Network (VPN) is complicated. I put a lot of time and effort into setting up OpenVPN on my own AWS EC2 instance, yet was still delighted to outsource the ongoing maintenance when I found my preferred privacy-focused VPN.
That said, there’s no better way to …

Wanted: ability to grep IRL, as in, grep -Hrnwiv soy frozen_food_aisle/
… Ok ok
- H: with filename
- r: recursive
- n: print line number in file
- w: match the whole word
- i: ignore case
- v: invert matching (select non-matching lines)